Researchers: Joe Tallett, Nico Agnese, Marion Habiby, Christopher Soo, and Maria LeRoy
Sometimes hope can get the better of reason, especially when it comes to offers like a free pair of shoes for simply downloading an app. However, as with many traditional malware lures, this hope is being exploited by a family of Android apps to distribute a novel new ad fraud botnet. In the final week of June 2020, the malware’s ad fraud operation—which silently loads ads in the background on infected devices—had upwards of 65,000 unwitting participating devices, spoofed over 5,000 apps, and was responsible for more than 2 billion bid requests.
The White Ops Satori Threat Intelligence & Research team identified and has been actively defending against the attack—which we’ve codenamed TERRACOTTA—since late last year. We’ve been devising and deploying protections against it for our customers, who are fully protected. Today, we are revealing the details of this scheme in an effort to broaden awareness for users, advertisers, and the cybersecurity community at large.
A spokesperson from Google offered,
“Due to our collaboration with White Ops investigating the TERRACOTTA ad fraud operation, their critical findings helped us connect the case to a previously-found set of mobile apps and to identify additional bad apps. This allowed us to move quickly to protect users, advertisers and the broader ecosystem – when we determine policy violations, we take action.”
Pumped Up For Kicks
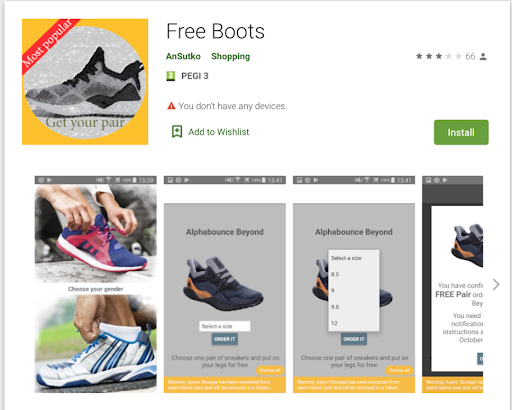
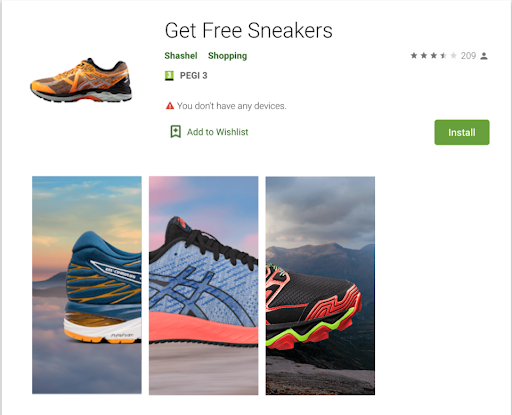
Starting late 2019, a family of Android apps showed up on app stores with an enticing offer (as seen in Figure 1) . Download the app, fill in your details, select a pair of shoes (or event tickets, coupons, even expensive dental treatments depending on the TERRACOTTA app), and in 14 days time those shoes will be mailed to your front door, for free, with no strings attached! What a steal, literally...
(click on any image in this report to enlarge)
Figure 1: The apps promise to ship the user their choice of high end shoes.
Source: Google Play Store
It sounds too good to be true, but clearly many Android users found the promise enticing enough to sign up (Figure 2):
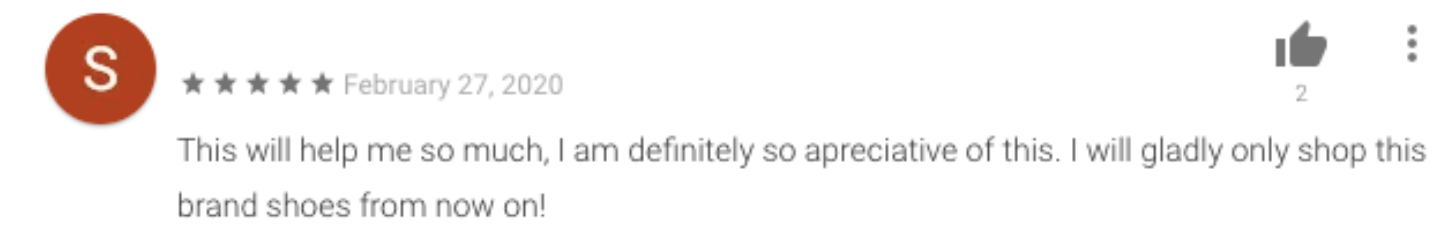
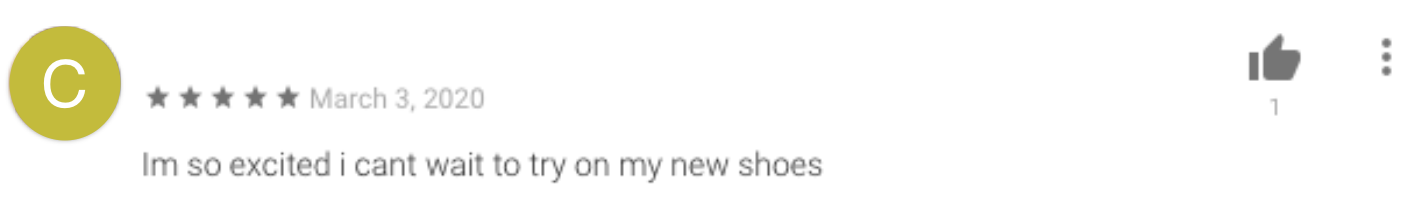
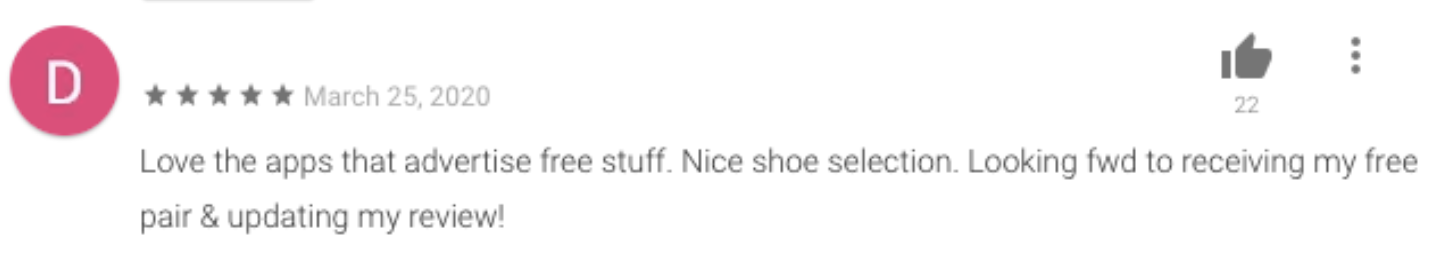
Figure 2: Reviews on the Play Store of seemingly happy customers awaiting their new shoes
Source: Google Play Store
Unfortunately, weeks of waiting for that knock on the door clearly started to take its toll and the glowing 5-star reviews from excited users quickly made way for anger (Figure 3) as reality started to creep in: is this app to which I supplied my name, address (and shoe size!) legitimate?
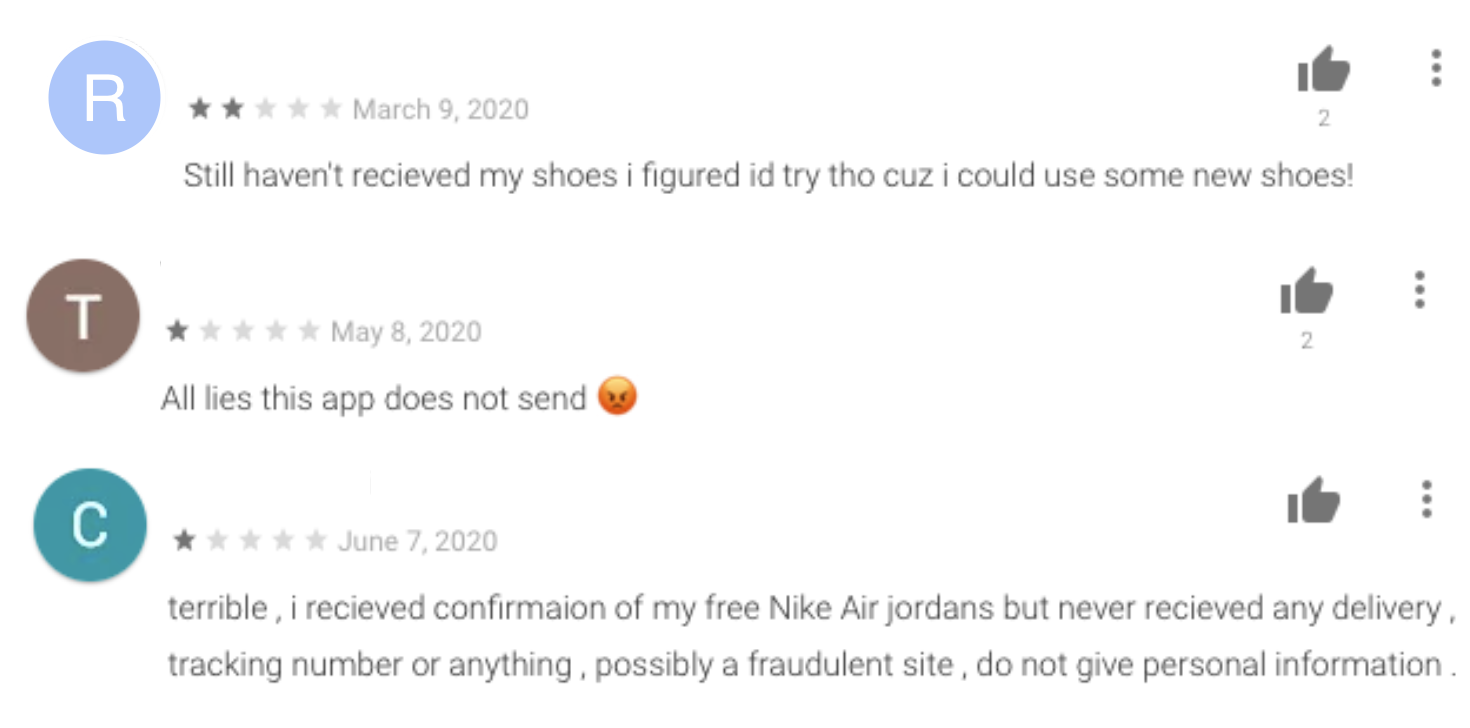
Figure 3: The 1 star reviews from folks who haven’t received any shoes. Some have caught on that this is a scam.
Source: Google Play Store
These apps weren’t really offering free shoes at all and users were left empty-handed (and barefooted). Many ‘scam’ apps like these across the internet lure users in to installing them under false pretenses, provide no meaningful functionality, and proceed to bombard their users with unwanted and intrusive ads. But this family of apps was different: the apps don’t report via Google Play that they are ad-supported, and no users were complaining of seeing unwanted ads. Further analysis of the app revealed no ads being shown and no obvious monetization mechanism. So for users, there was a sobering dose of disappointment when their shoes never came, but no real harm done, right?
Wrong.
Buy One, Get None
Upon further analysis by the Satori team, it became obvious these apps were a delivery platform for some other functionality, which was lying dormant even beyond the 14-day window of promised shoe delivery. The real free “product” surreptitiously sent to users was a box-fresh payload of ad fraud malware.
The real payload—a customized Android browser packaged alongside a control module written in the React Native development framework—is loaded onto the phone and used to generate fraudulent ad impressions, sold into the programmatic advertising ecosystem, and defrauding advertisers at scale (Figure 4).
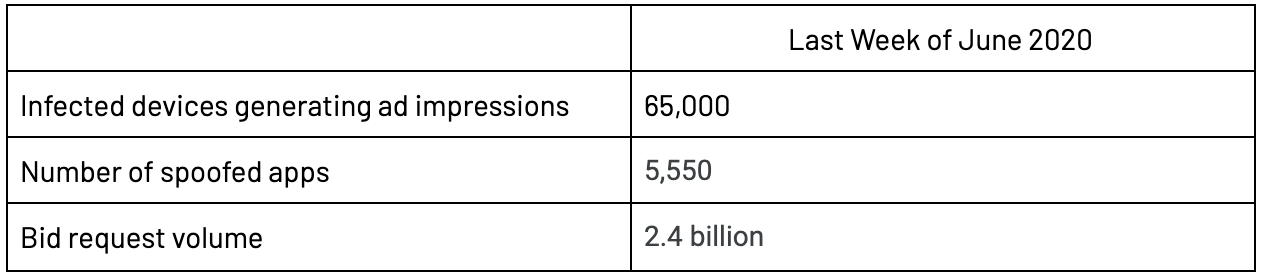
Figure 4: TERRACOTTA Summary Statistics as measured in June 2020
Source: White Ops Satori Threat Intelligence and Research
The operation of the TERRACOTTA malware is particularly noteworthy for its advanced know-how in pulling off ad fraud plausibly, indicating an experienced operation well-versed in the nuance of ad tech and ad verification.
Concealment of the true source of the inventory sold
To ensure reasonable revenue and advertiser interest, TERRACOTTA pulls off false representation of the traffic it generates, reporting the inventory as being from popular ad-supported Android apps (see appendix B for a list of the most commonly spoofed apps). This is not a new technique, but TERRACOTTA avoids two common methods of detection with its approach. Due to its use of a purpose-built Android Web View within which to render the ads, it is able to modify technical parameters commonly used to verify the application rendering the ad (shown in appendix B). It also steers clear of another industry-wide detection mechanism for this kind of fraud, ads.txt (or in this case app-ads.txt) by only misrepresenting as apps which don’t participate in ads.txt. To that end, while White Ops measures a global app-ads.txt participation rate of 71% (by impression volume) across mobile app inventory we protect, TERRACOTTA’s traffic only registered a 10% participation rate.
Highly configurable ad targeting parameters
The actors behind TERRACOTTA also show full awareness of the need for credible aggregate characteristics of their fraudulent traffic. The customized webview used to generate traffic is based on Chromium version 80, but the malware instead modifies its webview to hide this, and to appear as one of a preselected group of Chrome versions (most recently Chrome 78,79 and 80), according to a probabilistic model contained in the TERRACOTTA code.
As well as manipulating the aggregate breakdown of browser versions, TERRACOTTA controls click-through (or tap-through) rates on its ads (see figure 5). The following code snippet taken directly from the malware shows how it selects when an ad should be clicked as well as where on the ad the click should happen.
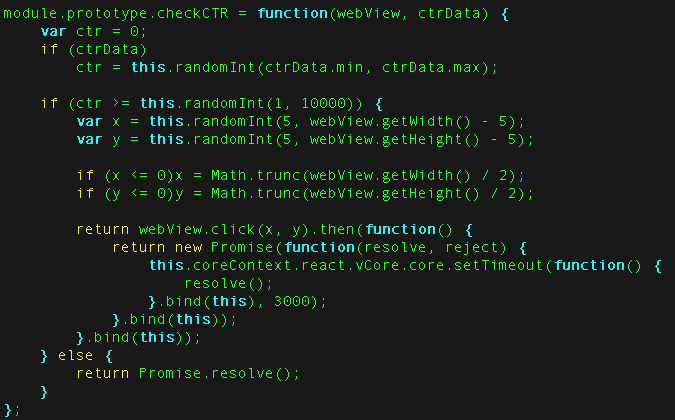
Figure 5: extracted JavaScript code controlling whether a click should be triggered, and if so, where.
Source: White Ops Satori Threat Intelligence and Research
Specific evasion of ad verification code
TERRACOTTA also exhibits one of the rarer forms of deception against bot mitigation, which is tag evasion. This is a similar technique to ad-blocking, but rather than blocking the loading of content from ad-serving domains (as an ad blocker does), the malware blocks the loading of content from ad-verification domains with the intention of suppressing fraud detection (see figure 6). Unless—as is the case for White Ops Advertising Integrity—the ad-verification vendor has specific defenses in place to counter tag evasion, they will lose all visibility into the fraud and be unable to monitor or defend against it.
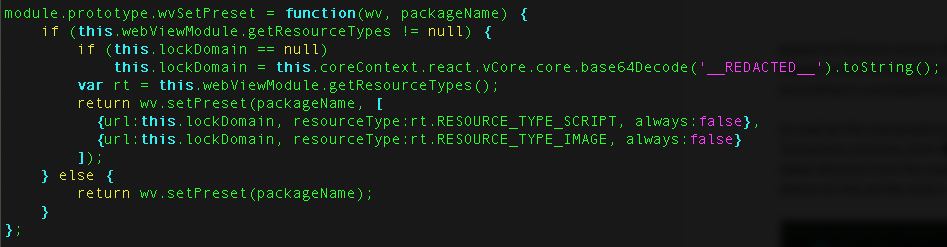
Figure 6: Extracted JavaScript code configuring TERRACOTTA’s customized browser to drop all scripts and images requested from a specified domain.
Source: White Ops Satori Threat Intelligence and Research
Perhaps worth noting is the deviousness of the tactic used to distribute TERRACOTTA. Imagine yourself in the fraudster’s shoes (pun intended) looking for an effective means of malware distribution: the promise of free shoes at a later date has all the hallmarks of a classic malware lure, offering a limited supply of something for nothing, and encouraging users to ignore their better judgement and click that button for fear of missing out. But this tactic offers other ‘benefits’: the 14 day waiting period for the shoes means users are happy to leave an app installed on their phone that has no real functionality. This means not only is it cheap to build the app’s ‘cover’ function, but the malware can afford to ‘lay low’ for a period before activating, making it much harder for users to attribute the bad behavior once it starts. As an added bonus for the bad actor, the activation delay trips up cybersecurity analysis too: unless the app is kept under observation for an extended period of time—which is costly—no bad behavior is observed and the malware stays undetected by the anti-virus community.
Return Policy
Following comprehensive takedown action by Google, the volume of traffic that we see observed from Terracotta has sharply decreased -indicating a successful disruption of the operation (Figure 7).
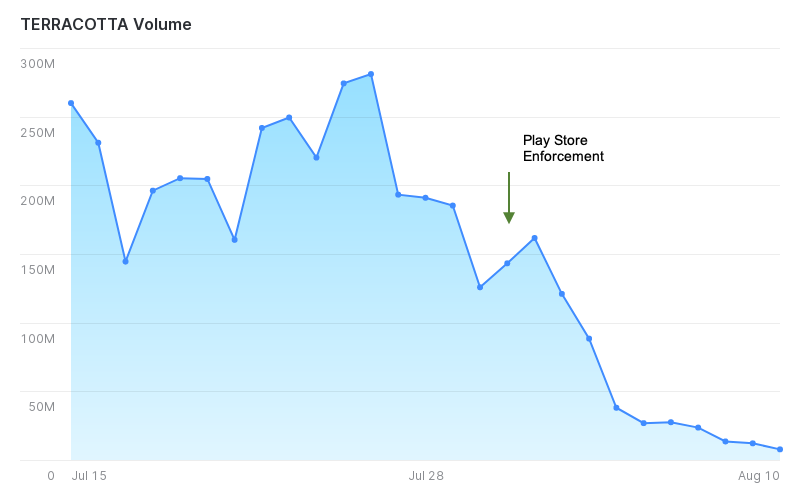
Figure 7: Bid request volumes as a result of Play Store enforcement
Source: White Ops Satori Threat Intelligence & Research team
That said, active TERRACOTTA infections do remain and are generating invalid ad impressions sold via RTB. The defenses we’ve deployed over the course of the operation means partners who use White Ops’ Advertising Integrity have been - and continue to be - fully protected against TERRACOTTA.
In order to further protect against what remains of TERRACOTTA, and prevent the scaling up of other operations like it, White Ops proposes some key actions that can be taken by various members of the ad-tech community:
-
App Publishers:
- It’s simple: adopt app-ads.txt. TERRACOTTA is an eye-opening example of fraudsters moving their activity towards unprotected areas of the ad-tech ecosystem. You can protect your inventory from being impersonated and monetized by fraudsters by adding an app-ads.txt file for your apps.
-
Advertisers:
- Ensure your ad verification partner has robust tag evasion defenses. As we’ve shown, TERRACOTTA and other sophisticated ad fraud malware are able to selectively avoid running code from ad verification companies, so a robust capability against this is something your fraud fighting partners should have.
- Only buy inventory from sources which are app-ads.txt verified. Attacks like TERRACOTTA take advantage of publishers who are slow to adopt the standard, so channelling spend towards those who have adopted can act as more incentive for adoption.
-
Members of the Antivirus / mobile security community:
- Due to the sophistication of this malware operation, the Satori team wrote an additional technical report to dive into the details of how the botnet evaded detection and how the malware worked. Please reach out to the Satori team for further collaboration and information sharing.
And lastly, as much as we all love a bargain, remember friends don’t let friends get scammed online. Talk to the people in your life that may need a reminder to tread carefully online and give them advice on how to spot a potentially fraudulent app. Educating all consumers is how we can fight bad actors, like the TERRACOTTA operators, from making their schemes lucrative. Fraudsters will continue to find new ways to gain access to devices and use data for harm, so users must stay smart. For now, we suggest a safer option: check out a shoe store instead.
Appendix A
The following is a traffic capture of TERRACOTTA showing the communication with its Command & Control (C&C) server.
The first HTTP request/response below shows the C&C specifying which app to spoof (in blue) and the desired click through rate parameters (yellow). The second request/response shows the bot subsequently falsifying its Chrome version (blue) and falsifying its app ID to that specified by the command and control server (red).
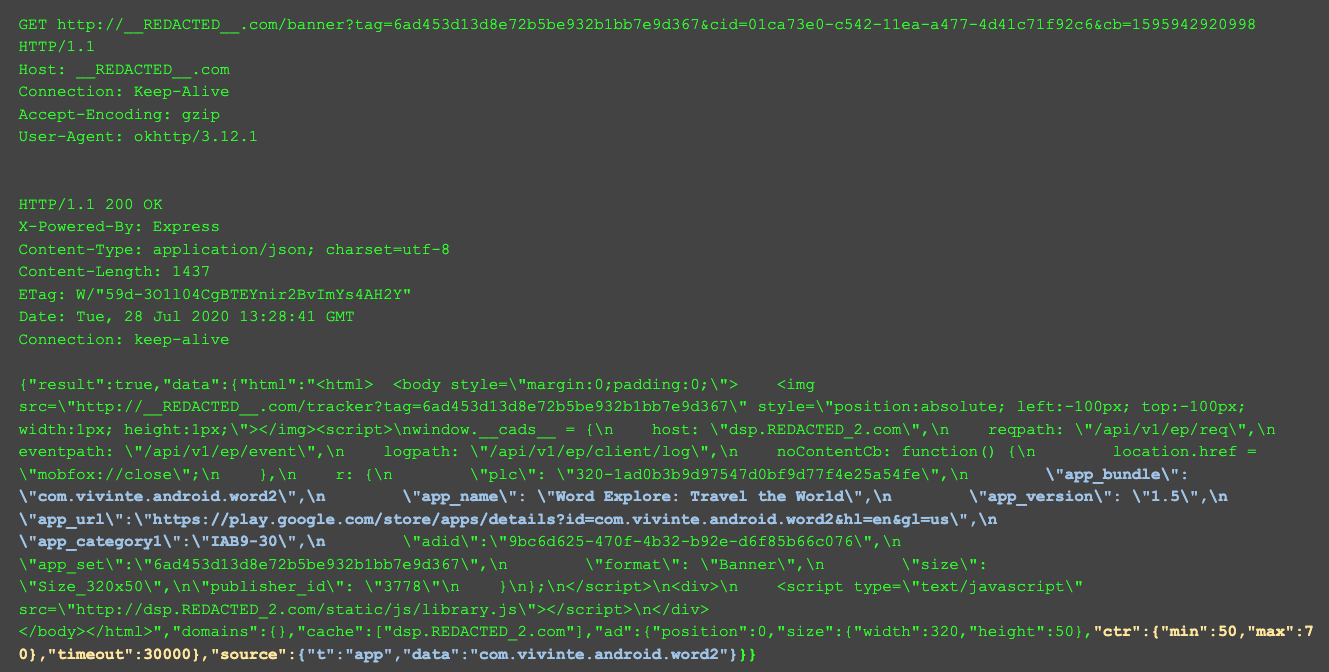
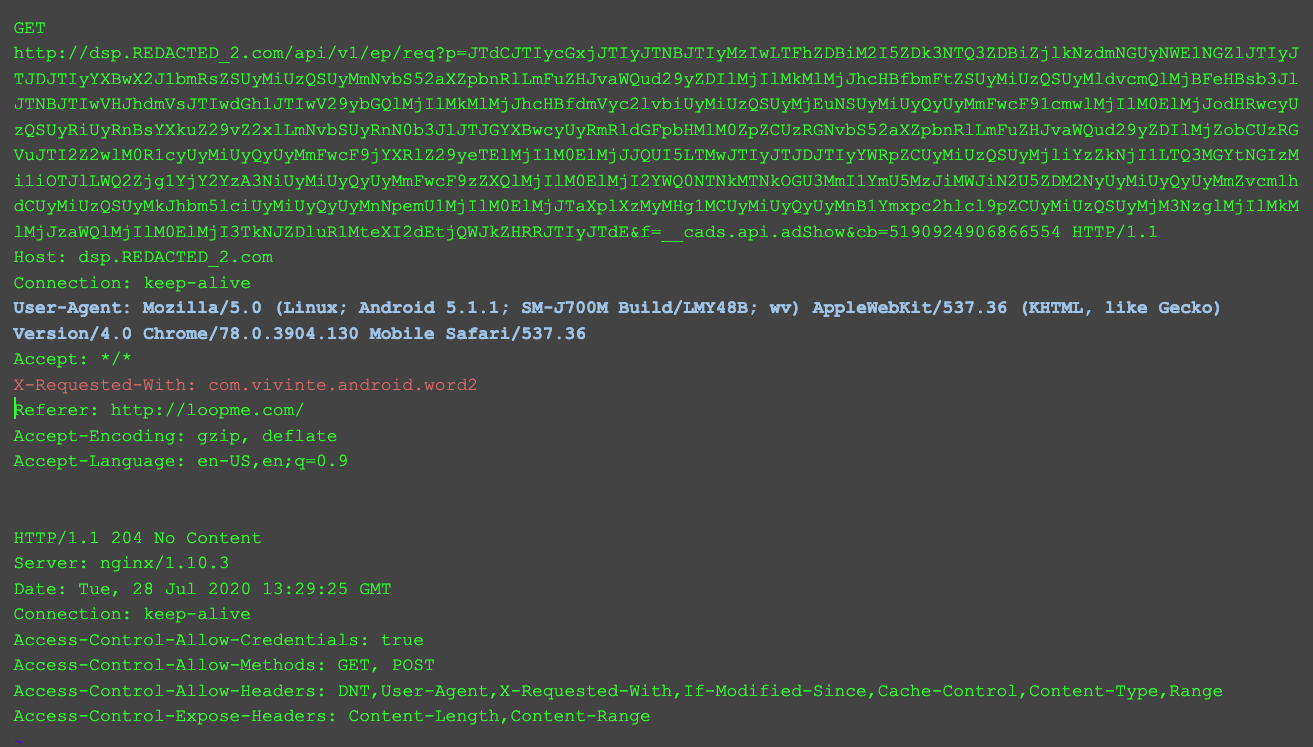
Appendix B
Apps most often spoofed by TERRACOTTA
TERRACOTTA masquerades as thousands of other apps in order to launder its inventory. We’ve selected the most common app IDs used by TERRACOTTA for both June 2020 and July 2020 below.
Note: the TERRACOTTA apps give falsified app identifiers with the following values. The apps below are legitimate apps and the victims of the TERRACOTTA scheme, and the list should not be used for blacklisting.
July 2020 (20 most commonly spoofed apps):
com.blapp.videodownloader
softin.ny.women.fitness.miss.bikini
com.record.my.call
media.music.mp3player.musicplayer
luxury.art.effect.snapchat
com.bookmark.money
gallery.photomanager.picturegalleryapp.imagegallery
beautyrooom.filtersforselfie.sweet.face.camera
com.tumblr
anime.face.changer.cartoon.photo_editor
filter.selfie.camera.photo.stickers
com.livevideocallvideochat.livevideocalllite
christiansingles.match.dating.meetfriends.chat
live.wallpaper.t910001780
com.bigoceanstudio.vpn.unblock.master.unlimited.proxy.hotspot
com.yellowpages.android.ypmobile
com.glasses.tabatatimer
com.science.wishboneapp
cofs.filters4snapchat
com.deccanappz.livechat.indianchat
June 2020 (20 most commonly spoofed apps):
com.tiramisu.driftmax2
com.eastidahonews.id3165
com.lbrc.PeriodCalendar
com.bestzippers.gold.lockscreen.zipper
com.lose.felly.fat.burn.workout.home.diet.plan
com.peoplefun.blockscapes
com.worldgymfitness.resistancebandsworkouts
com.peoplefun.wordsnacks
com.seagames.dominoqq
eu.livesport.MyScore_ru
app.sarhne.com
com.twobikesgame.twobikes
photo.video.instasaveapp
com.jrzheng.supervpnpayment
com.dbSoftware.siepro
com.home.design.interior.house.mansion.myhome
com.kmplayer
kr.co.rinasoft.howuse
com.nu.launcher
com.wescan.alo