Twoshu, Electric Boogaloo
Read time: 3 minutesSatori Threat Intelligence and Research Team

The White Ops’ Threat Intelligence team recently took a look at six HiddenAd apps shared by ESET Research. The apps were posted on the Google Play Store in mid-August 2019 and were taken down in the beginning of September. Our team analyzed the apps and found that they contain a new version of an old friend. We’re dubbing this new version “Twoshu”, following our original reporting on the Tushu Software Development Kit (SDK) in our Another Day, Another Fraudulent App post.
During our original dynamic analysis, Tushu was seen serving out-of-context ads. Static analysis of the code revealed that the SDK is capable of running while the screen is locked, generating hidden ads. The new Twoshu has similar code and now features single-byte XOR obfuscation techniques while the previous version was easily viewable in clear text. Twoshu also added anti-analysis tools in addition to the code obfuscation techniques.
A Closer Look at the Obfuscation
Twoshu employs single-byte XOR obfuscation techniques to slow down analysis. Instead of storing important strings in clear text within the dex file, there is a call to a decoder function with one of the many statically-assigned byte arrays.
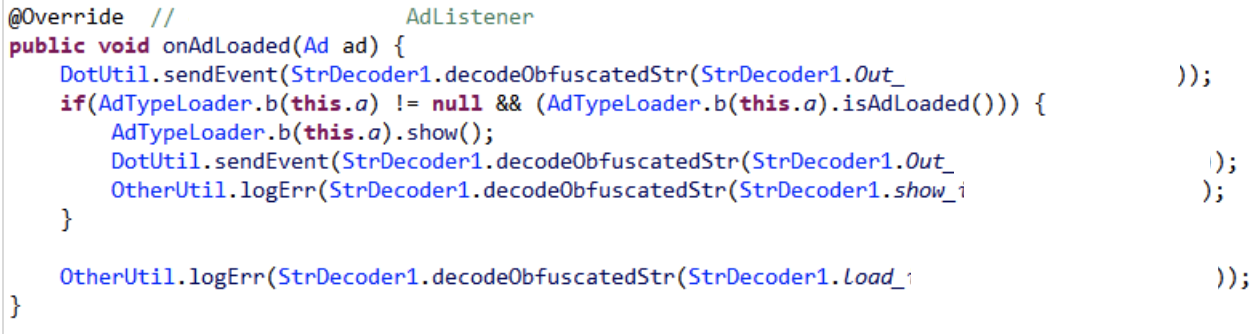
Figure 1 – Example usage of the string decoder
Source: White Ops Threat Intelligence
Anti-Analysis
Twoshu includes code from the Chinese open source project, EasyProtector, to determine if the device is an emulator. The code enumerates all installed packages on the system and checks them against an internal list of antivirus products. The code also checks to see if the device is connected to known antivirus (AV) Service Set Identifiers (SSIDs), see Figure 2.
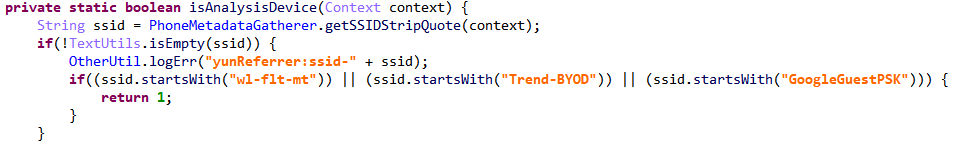 Figure 2 – Checking against known AV SSIDs
Figure 2 – Checking against known AV SSIDs
Source: White Ops Threat Intelligence
Finally, Twoshu will not run on a device that has fewer than ten apps installed, or more than three apps containing “.test.” in their package name.
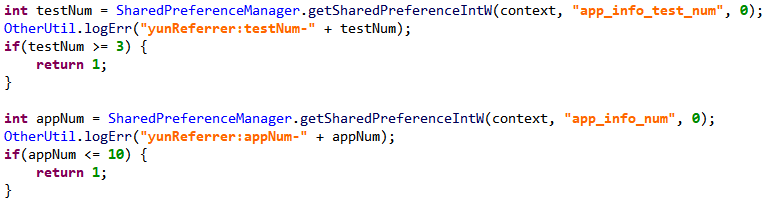 Figure 3 – Checking how many apps are installed and how many have .test. In their package name
Figure 3 – Checking how many apps are installed and how many have .test. In their package name
Source: White Ops Threat Intelligence
These techniques are typical of malicious apps trying to avoid detection. These anti-analysis techniques are not present in the original Tushu releases.
Similar to the previous version of Tushu, this new version logs an impressive amount of information from GPS coordinates to wifi SSIDs and device International Mobile Equipment Identity (IMEI). The White Ops Threat Intelligence team will keep monitoring Tushu SDK for further attempts to evade detection.
Researched and written by John Laycock, Inna Vasilyeva, and Ian Palleiko.
Indicators of Compromise
Hash values:
697B1AA0748E75A13F1FFC92DD048E5E
193A1B24952CBE1A4BA1E39CBCE25535
8715F35C6903A8DEC1D094B7AE82C07D
5BFD131E606D6FE2E325AC690E4DE185
E8B933EB2F57753EF7948AB565FFD897
DE7537D941266798371F570E2B9F2265
Domains:
h5play[.]top
1bz[.]cc